What is Shadowsocks, and why I prefer it over Wireguard
Why use Wireguard when watching Netflix is all you want?

In one of my older posts, I talked about using Shadowsocks in conjunction with Wireguard to bypass firewall. That works, sure, but when considering what people usually use Wireguard for, the redundency of this setup becomes apparent. People use Wireguard to visit geo-blocked websites! (or hide IPs in general) I mean yes, Wireguard can do this. So why bother with Shadowsocks?
What Wireguard is good at
Wireguard is one hell of a beast. It is a fully fledged Virtual Private Network (VPN). Unfortunately at one point, someone has to ask this question: what even is a VPN?
First, let's imagine the Internet: it's a chaotic space, with plenty of subnets, firewalls, maybe even MITM.
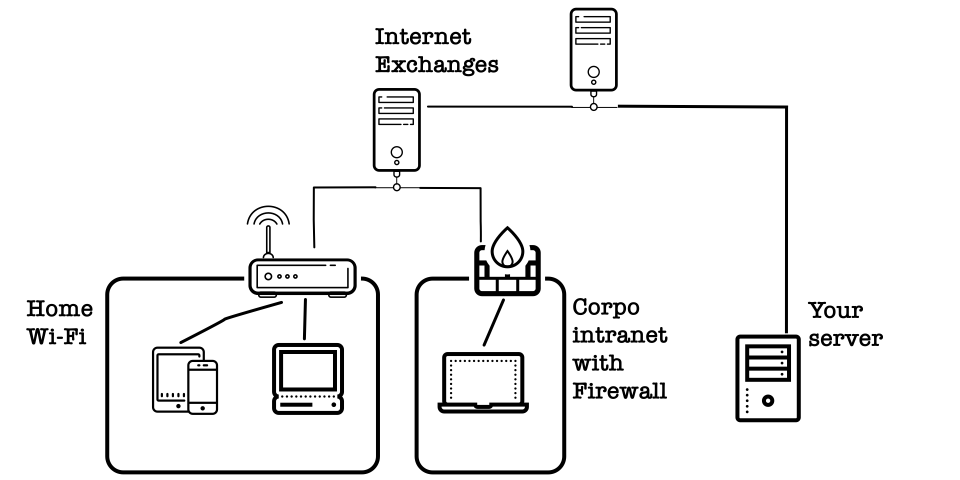
As the picture shows, it's not easy for your devices to communicate with each other. Each TCP message needs to go through (multiple) routers, firewalls, Internet exchanges, etc.
In this chaotic place, VPNs allows you to create a virtual network for all your devices across the Internet. It's like a second, secure Internet on top of the existing Internet. All information transmitted within a VPN is encrypted and cannot practically be deciphered by outside parties.
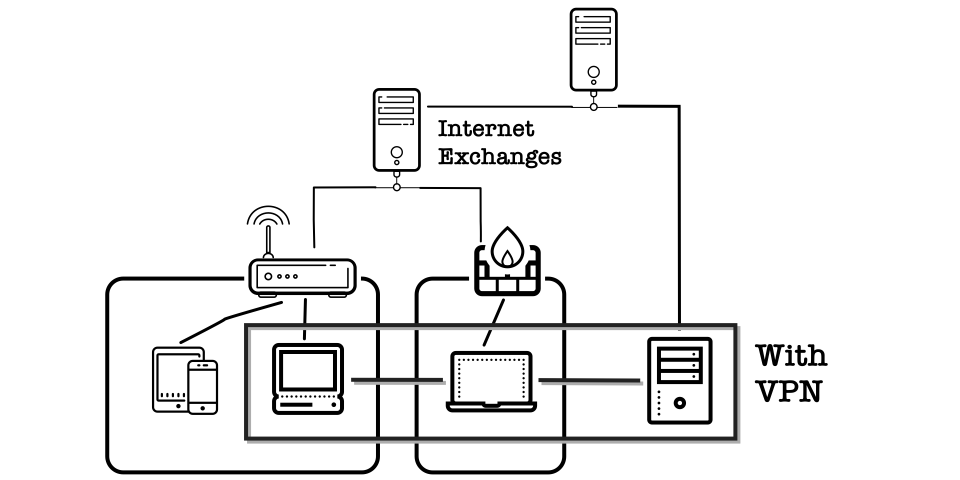
And Wireguard made this possible. Well, there is OpenVPN, but we don't talk about that.
Wait, how does establishing a secure network between your computer and your server allows you to browse US Netflix?
That's right. It doesn't.
The usual VPN setup that uncensors websites involves an extra step: forwarding all network requests from your computer to your server (which hopefully can access geo-blocked content). This allows all traffic between your devices and the server to be automatically encrypted by Wireguard.
Why not Wireguard
So why not just use Wireguard then? Although using Wireguard on trivial things such as unlocking geo-locked content is kind of undermining Wireguard's true potential, it's not like such use is forbidden, no?
It all comes to these two factors: speed and and anonymity.
Due to performance issues with TCP-in-TCP, Wireguard only operates with UDP packets. Usually this is fine, but in congested network environments (e.g. LTE) UDP packets might be deprioritized or simply dropped. This negatively impacts Wireguard's latency and throughput.
And of course, Wireguard traffic is not obfuscated. This is commonly an issue in countries with active censorship, as Wireguard traffic can be easily sniffed out by Deep Packet Inspectionand dropped afterwards. Lesser known fact is that even in countries with free speech, companies or ISPs might disrupt Wireguard traffic for security reasons (or for no reason at all).
Shadowsocks, a lightweight proxy
Shadowsocks was originally written by clowwindy, a Chinese netizen. Sadly they were persecuted to delete shadowsocks's original code and are probably in jail. No one knows for sure. Shadowsocks, as a project, continued to exist. It excels at one task: circumventing censorship to visit blocked websites.
As such, shadowsocks is made to be as lightweight as possible. This helps reduce its CPU usage, and if you are on a mobile device, prolong their battery life.
Similar to Wireguard, Shadowsocks encrypts traffic to ensure both the integrity and authenticity of the data. Unlike Wireguard, Shadowsocks can operate on both TCP and UDP. Even better, shadowsocks supports obfuscation out of the box. Not even your ISP can tell if you are using Shadowsocks or not!
As everything is run in user space, shadowsocks servers can run with less system priviledges and is thus technically more secure than Wireguard.
But the best thing about Shadowsocks for me is this: ease of use.
Shadowsocks: an easy-to-use proxy
As shadowsocks binaries are portable, you only need to download and run that binary to setup a shadowsocks server. Of course, this means setting up shadowsocks as a docker container is simple as hell.
A shadowsocks server is also easy to configure. All you need is the port for shadowsocks to listen to, and a password. For Wireguard, you need to generate a public key/ private key pair, and add all your devices' public keys into your server's Wireguard config. For shadowsocks, a password is all you need.
Shadowsocks also has a multitude of clients for each operating system. Even better, those clients supports "plugins", or extra obfuscations on top of the shadowsocks base protocol in case its default obfuscation is not enough.
Hilariously, I often leave shadowsocks on while on LTE network. Although T-mobile tends to limit Youtube's video quality, this does not happen at all if I'm on shadowsocks.
So what should you use?
It's simple: If you only want to visit blocked websites or contents, use shadowsocks. If you need to communicate with devices behind firewalls, use Wireguard. If your devices also happen to reside in a country with active censorship, use shadowsocks on top of Wireguard.